-

Cybersecurity Pantomime
There are times when I say to my clients, “That sounds like security pantomime”, and I realise that quiet a few have not understood what I mean. Cybersecurity Pantomime, also known as Cybersecurity Theatre, is a term that encapsulates the scenario where security measures, despite their flashy display, fail to reduce risk in a substantial…
-

Understanding the Nuances of Security and Privacy
While privacy and security are often discussed interchangeably, they are distinct concepts with nuanced differences. Security typically revolves around controls that provide three key guarantees: Confidentiality, Integrity, and Availability (CIA). While privacy is giving the data respect and forces you to make considerations before collecting, storing, using, or accessing this sort of data, whether it…
-

Home Network – Reverse Proxy
The gateway to many of the services running in my infrastructure is my reverse proxy. For years, I have been running an Nginx setup, but have recently switched to running the same proxy I generally use in production systems. Traefik Proxy. This is partially because I need a simple reference system that I can use…
-
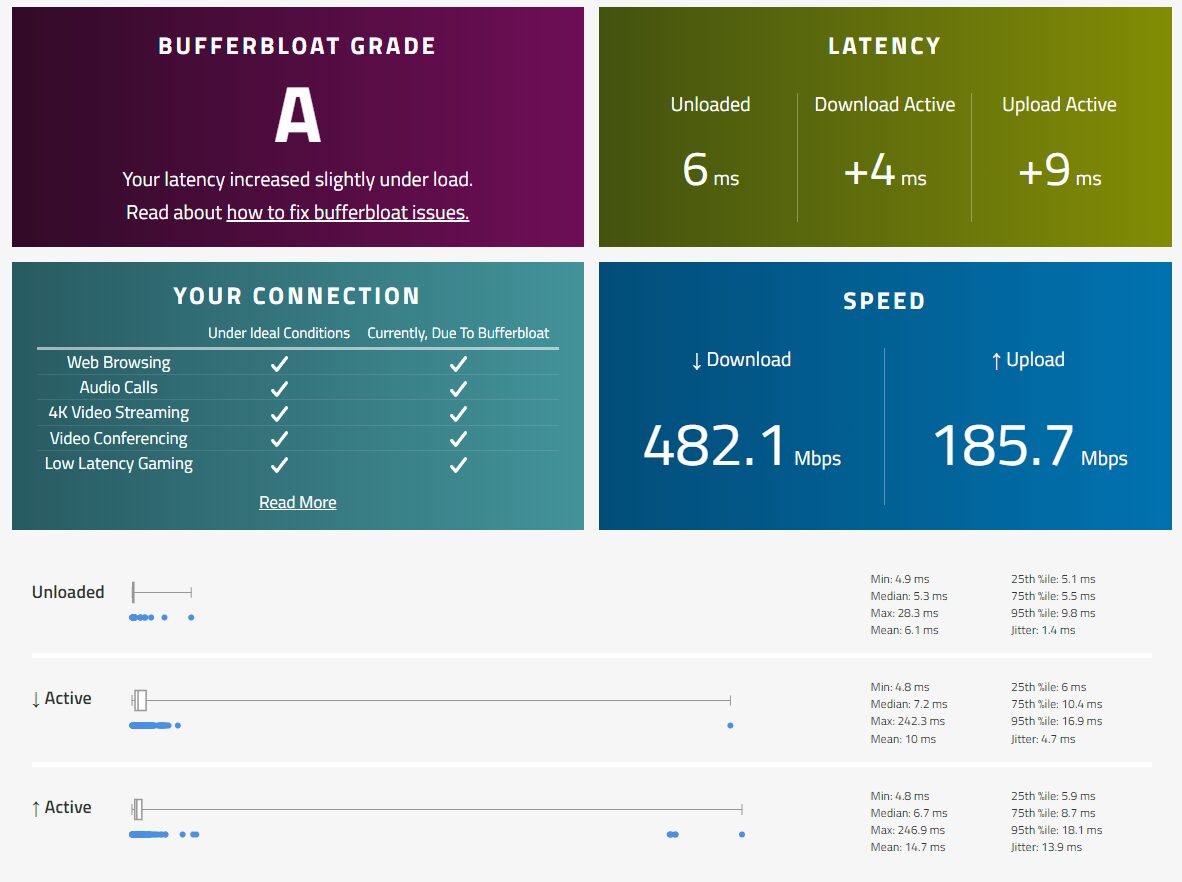
Home Network – Router
My home network is one that I have setup to provide as much security, for the least amount of money. My home internet connection is a 500/200Mbps connection on a FTTP NBN with Aussie Broadband. In order to meet both the least amount of money, and as secure as possible I needed to look at…
-

Home Assistants HACS and IPv6 issues
Home Assistant (HA) has a fantastic extension ecosystem that uses the Home Assistant Community Store (HACS). Most of the repositories are held on Github that have specific files copied down to your HA instance. Attempting to install a new front-end card (button-card) I kept getting a timeout issue, this seemed odd, so I SSH’d into…
-

How to use dotnet and Traefik to connect a legacy PHP application to AWS S3
One of the legacy systems that I needed to assist a client on, has a business-critical application written in PHP 5.2 hosted on a CentOS 6 VM. This host machine has an old version of OpenSSL and does not connect to many modern endpoints that require strong ciphers and TLS 1.2 or higher. Further, loading…
-
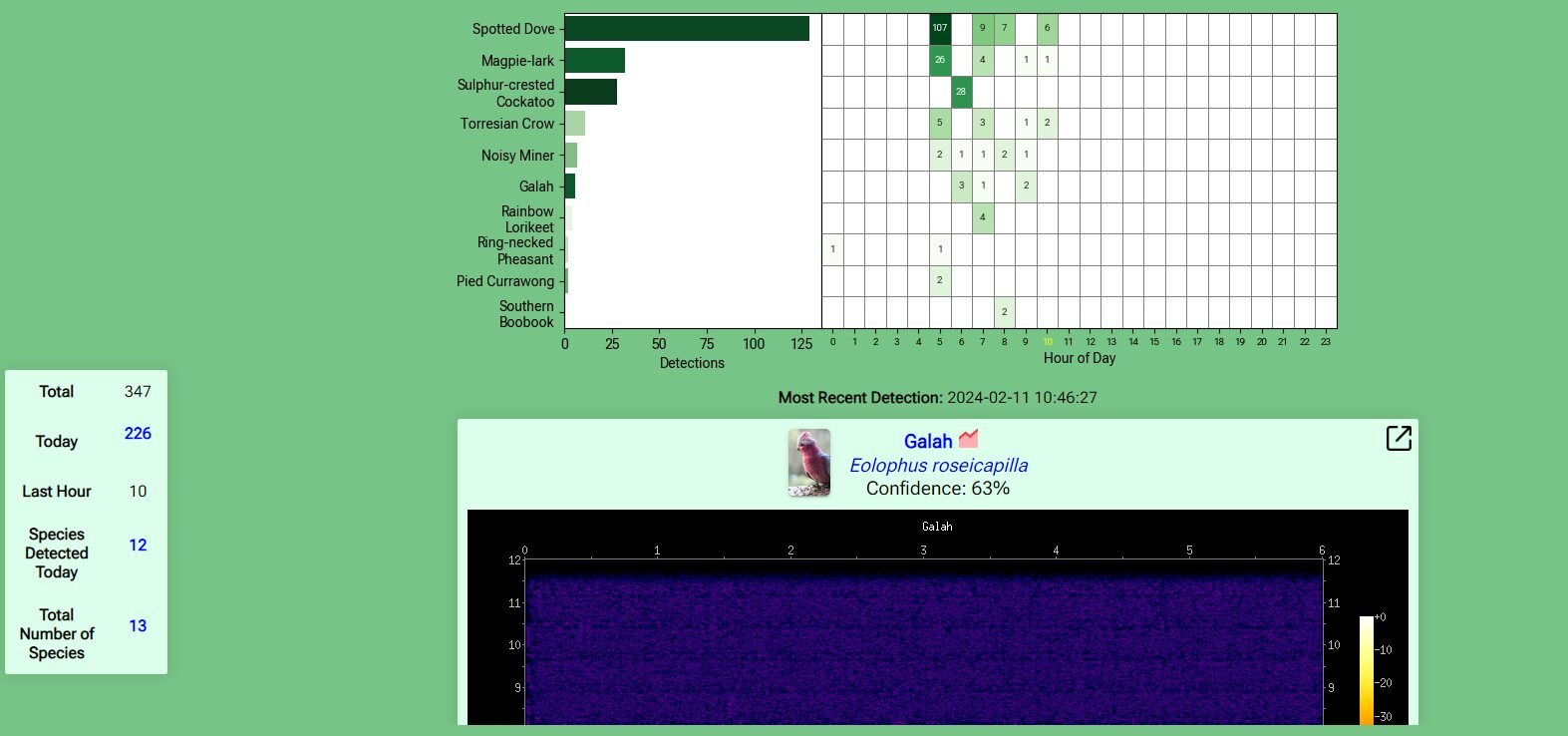
BirdNET – Detecting the birds in the backyard
What started as a way to know when the little flock of Superb Fairywrens would visit the garden, soon turned into something to know what birds are visiting. I could not spend all my time looking out the window waiting for the little fluff balls to chirp and hop about. I had a thought that…